Malware Analysis Tools, Part 2
Note: my article was originally published on IstroSec blog
In the second part of our overview we continue with the selection of the most used and most usable malware analysis tools. Moreover, we select the tools which are freely available. This time, we focus on tools for analysis other types of the files instead of the native binaries from the previous blog.
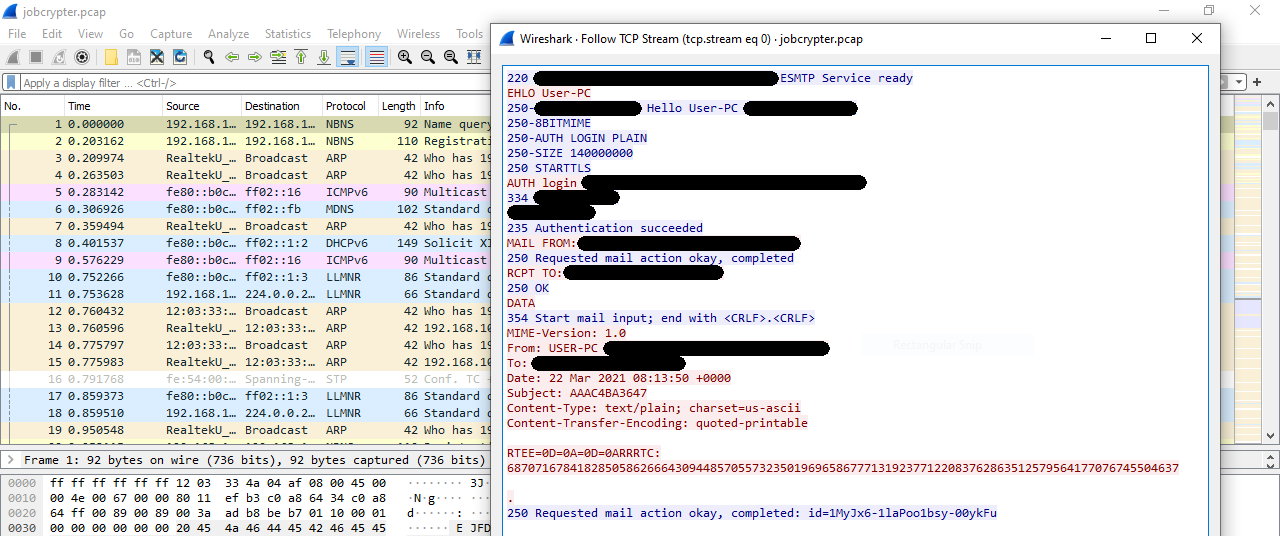
Wireshark
Wireshark is the well known tool for analysis of network traffic and network protocols. It can do a realtime capture and analysis as well as dump the captured traffic for later offline analysis. It supports powerful filters and thanks to the integration of plenty of the dissectors it can understand and parse a wide range of network protocols. Last, but not least, it can decrypt SSL/TLS traffic, if we provide private key associated with the server certificate. This is especially useful in case of malware traffic analysis, when we want to analyze the communication with C&C server - with a SSL proxy we can intercept and decrypt its traffic.
dnSpy
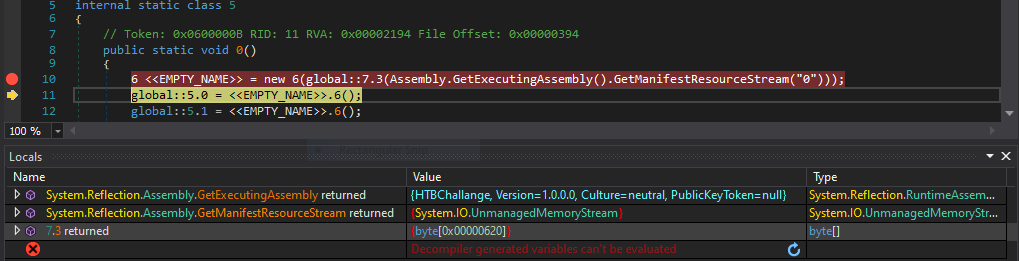
Nowadays this tool is almost archaic for someone. Decompiler, assembly editor and .NET debugger dnSpy was very popular tool used not only for malware analysis. However, in December 2020 it was discontinued and the Github repository was archived. On the other hand, the latest release is still available for download. For analysis of samples based on older .NET versions it is still sufficient, but we need to keep in mind that no new features or support for newer .NET platforms will come.
It is also suitable as an educational tool because of its intuitive user interface with good support for cross-references from and to analyzed functions.
Because dnSpy is deprecated now, there are couple of alternatives: dotPeek, ILSpy or cross platform MonoDevelop which is available for .NET malware analysis on Linux, too.
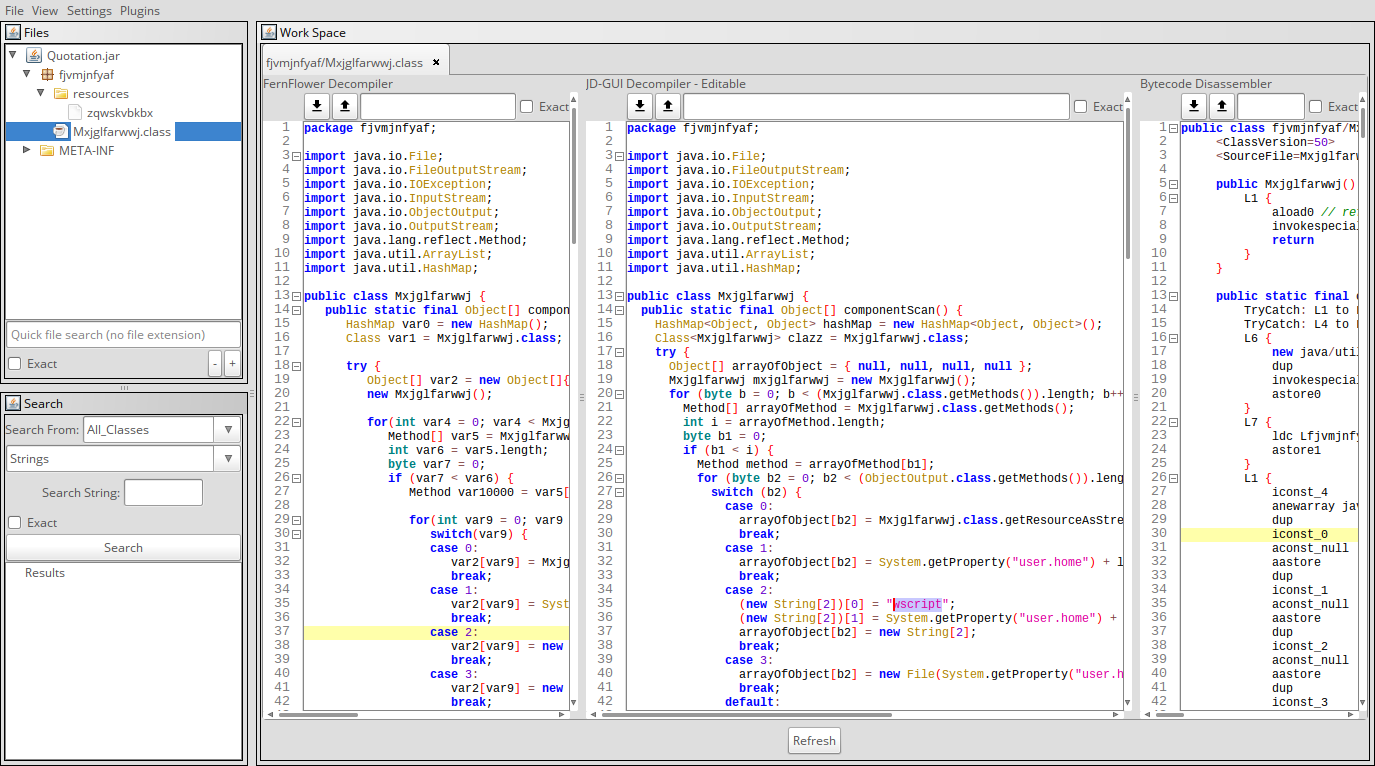
Bytecode Viewer
Java (and Android applications) decompiler, bytecode editor and compiler. It integrates several free tools into the unified user interface. It supports 6 Java decompilers (JD-GUI/Core, Procyon, CFR, Fernflower, Krakatau, JADX-Core), it can easily edit Android APKs with its Smali/Baksmali and dex2jar integration. One of the best feature is the multi-pane layout, in which the analysts can view the output from up to three Java decompilers or bytecode viewer. This is particulary useful when some decompilers can not decompile something, or if their output is not 100% correct. Then, the analysts can compare outputs from different decompilers side by side and figure out the purpose of the original program.
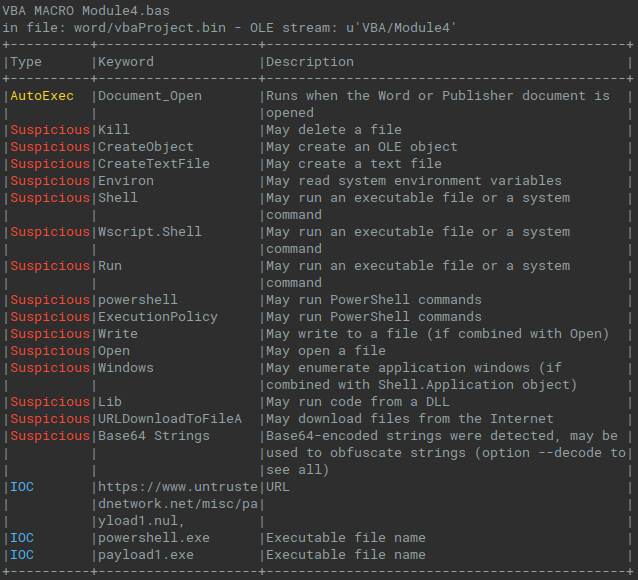
Oletools
Office documents are very common source of malware infection, especially Microsoft Office documents, spreadsheets and presentations. Newer file formats (Office Open XML, files with the extensions .docx, .xlsx, .pptx) are basically ZIP archives with XML and other files inside. Older format, OLE or OLE2 (Object Linking and Embedding, Compound Document File Format) are more binary files and they are still used by the attackers for malicious purposes.
When we need to analyze office files, there is very good tool, or set of tools, called oletools. It is a collection of small Python programs for static analysis of files, extracion of objects from OLE and RTF files, and, probably the most recognized tool olevba for extraction and analysis of macros from OLE and OOXML files.
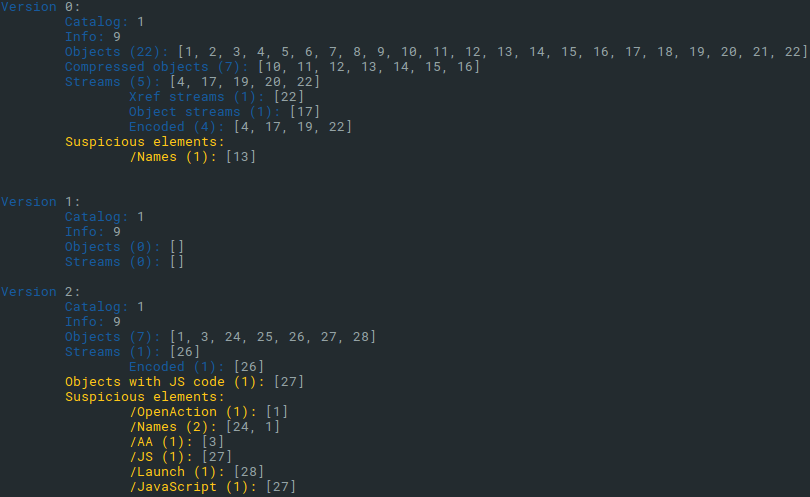
Peepdf
PDF files are another type of the documents misused by the attackers for malicious purposes. They can contain exploits or embedded malicious objects and files. For examination of the PDF files structure, we have more options. One of the best and easily available is the peepdf tool, which is also installed in the malware analysis Linux distribution called REMnux.
It supports both interactive and acript mode, it is capable of list and view all objects in PDF file. It highlights suspicious elements and it can extract them. For those analysts, who prefer GUI tools for exploring PDF structure, there is an alternative called pdfwalker, however, it is not as powerful as peepdf.
Conclusion
In the second part of our miniseries we have introduced another 5 free tools for malware analysis. This time, we focused mostly on analysis of .NET and Java applications and Microsoft Office and PDF files. Together with the 5 tools from our first post we proposed the overview ot the Top 10 tools for analysis of most common malicious files and network traffic.
Moreover, we mentioned several alternatives and more complex toolkits, including REMnux, the specialized operating system for malware analysis. Of course, professional malware analysts often uses much more tools including their own scripts for analysis of suspicious files, but this is out of scope of this Top 10 overview.